I have a secondary network from my ER605 router, this is used that the connected device, a raspberry pi, can be isolated. I use it to quarantine and scan incoming files from dubious sources (such as my in-laws perpetually malware afflicted computers). I need to be able to access the pi and exfiltrate scanned files to my primary network. I plan on using VNC for access and putting ok’d files directly on my QNAP NAS via SMB share.
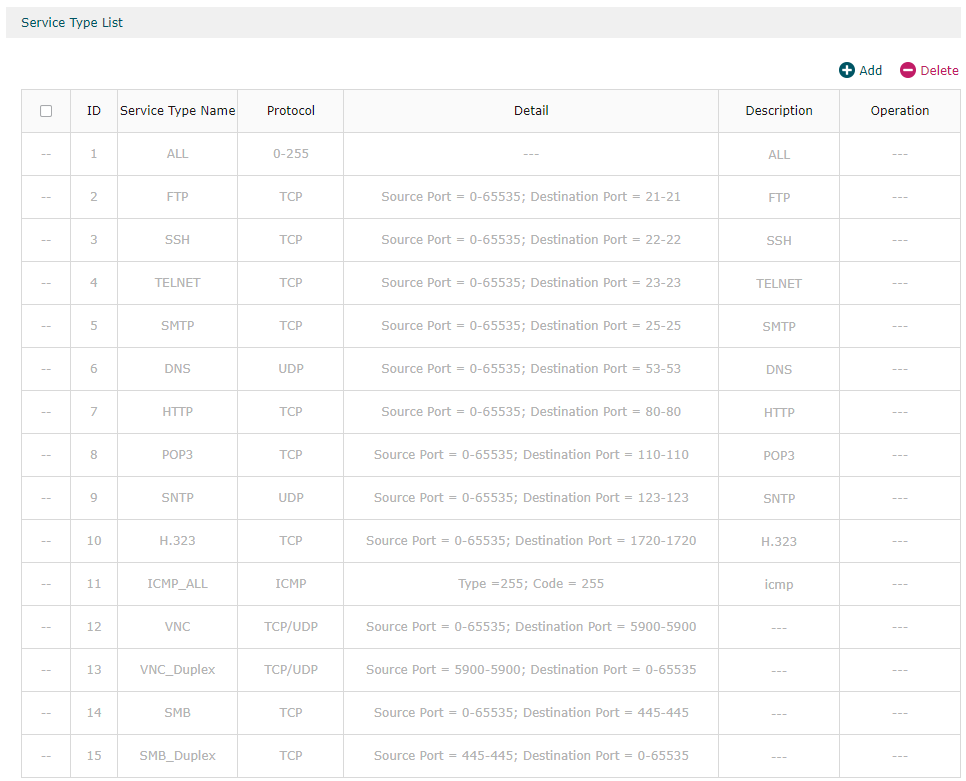
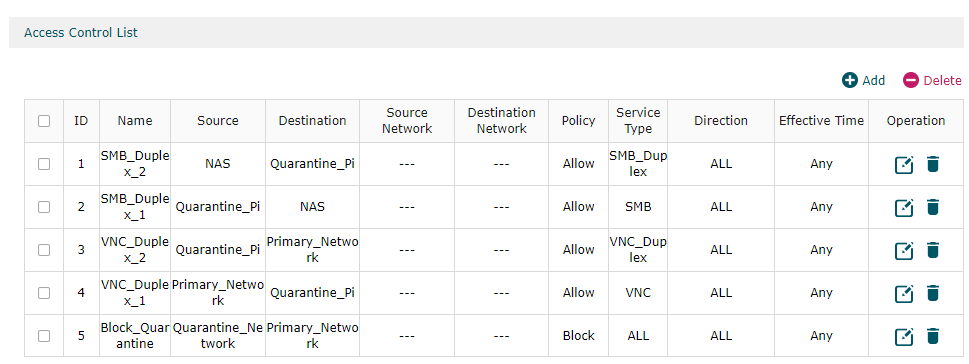
ACL rule 5 blocks communication from the quarantine network to my primary network. In order to get VNC to my quarantine pi from my primary network I initially added rule 4, which was insufficient (online reading suggested I needed an ACL for return messages), so I added a version of rule 3 that referenced the VNC service, and that still failed. On a whim I tried creating the VNC_duplex service definition which swaps source and destiation port and changing rule #3 from VNC service to VNC duplex, and viola VNC worked!
I’m pretty happy this is working, but I’m not certain why, or if it’s secure. Am I correct in understanding that ACL rule 3 allows for a malicious script to send a message from any port on the raspberry pi to port 5900 on any device on my primary network? What’s the semantic way of understanding this, and could it be made more secure?
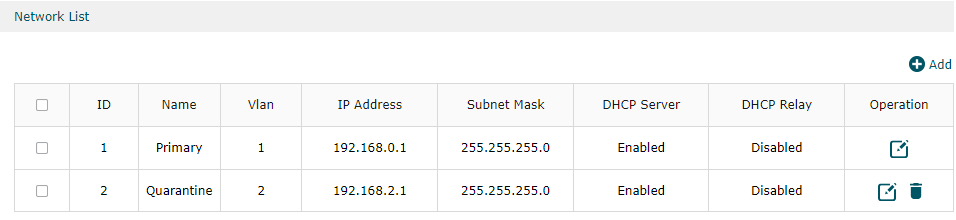
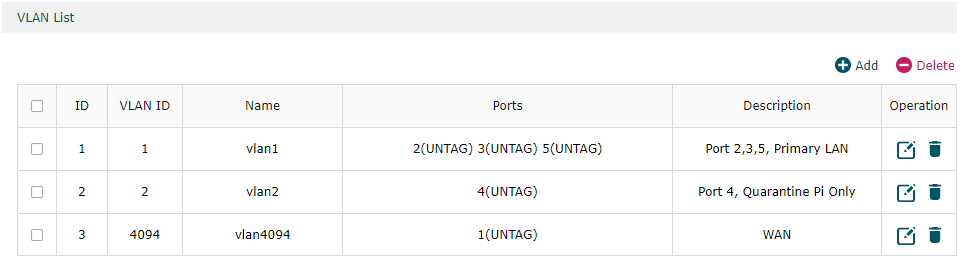
My network and VLANS:
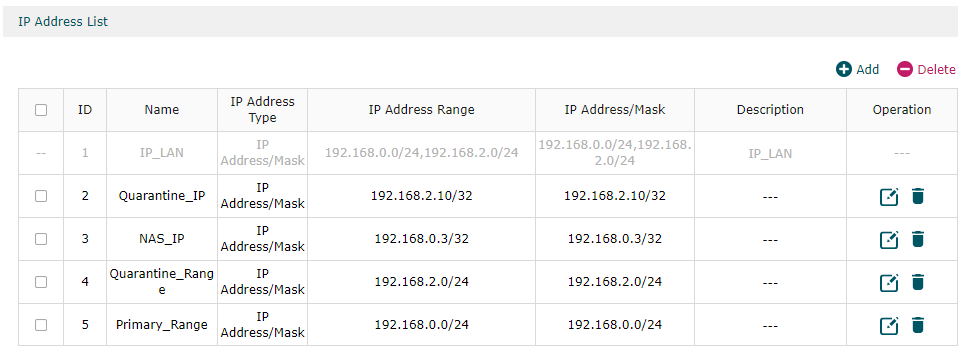
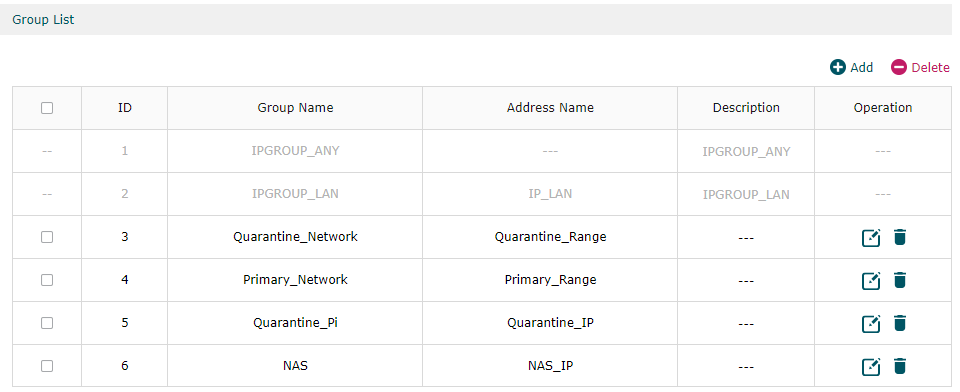
I have set up some ip ranges as well to describe areas of my network that I want to segment/grant access to:
My service types (the last four are custom entered by me):
And finally my ACL: