Is AD CA (AD Certificate Services properly configured) all that’s needed for internally facing sites to be trusted w/o any additional configuration on domain-joined clients?
Say:
- Active Directory Certification Authority is properly installed
- Certificates to internally facing sites are properly issued and are valid
- No other certificates (e.g. “retail” SSL certificates from Digicert or others) are used
Will browsers such as current versions of Chrome, Edge, Safari, etc. on AD-joined computers “trust” those internally facing sites? (E.g. vCenter or SolarWinds web UIs.)
If not, what are the steps to get them trusted?
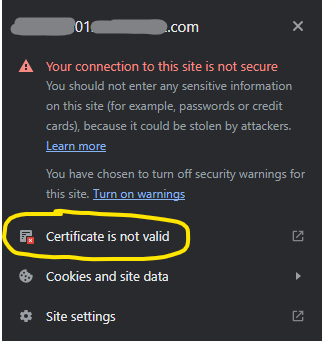
If yes, and the certificates still show as invalid, what are the steps to troubleshoot the issue? (Which logs to look at, how to isolate the issue to a specific part in the cert chain and how to remedy it from there, etc.)
Reason I ask: the AD CA seems to be functioning well as domain-joining new computers is smooth with no issues, and existing domain services seem to be working OK. However any internally facing sites we have are flagged as not secure despite seemingly having valid AD CA certificates.
(Windows Server 2016 with AD DS, CS roles installed, CS configured.)
P.S. I anticipate the above info may not be enough to determine what’s wrong and will be happy to supply more information and amend this question.
P.P.S. I am on my 3rd day in this rabbit hole and saw in several places that the answer to the title question might be a “yes” – but have yet to find it stated authoritatively in MS AD docs, or demonstrated somewhere, and have yet to find guidance on how to troubleshoot common issues.